SIEM Optimization Strategies
 20:24
20:24
Related videos
Windows Event Collector clustering with Syslog-ng
Use Syslog-ng to enable scaling, redundancy, and load balancing for Windows Event Forwarding
Duration: 14:45
syslog-ng Introduction to Log Management
Some people think log collection and log management should be part of the SIEM toolkit. We beg to differ, and we have some good reasons to. Neil will introduce the concept of log management and how it completes the ecosystem around logs in an enterprise setting.
Duration: 12:49
syslog-ng and Microsoft Sentinel
Learn how to use the Syslog-ng Azure Sentinel destination driver to ship logs directly into Sentinel via API
Duration: 11:16

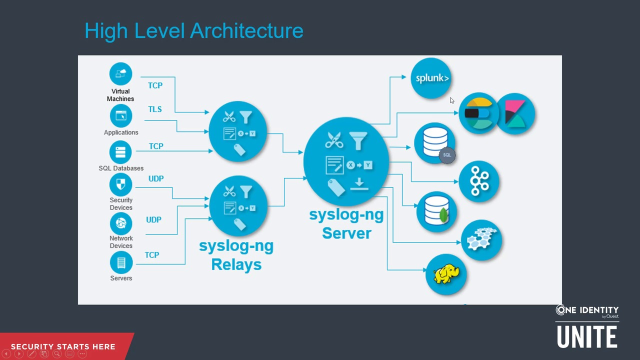
Scaling to large networks with syslog-ng
syslog-ng Premium Edition delivers the log data critical to understanding what is happening in your IT environment. Whether it's user activity, performance metrics, network traffic or any other type of log data, syslog-ng can collect and centralize it. You can remove data silos and gain full-stack visibility of your IT environment.
Duration: 02:38
Optimize your SIEM with syslog-ng
Whether it's user activity, performance metrics, network traffic or any other log data, syslog-ng can collect and centralize log data. You can remove data silos and gain full-stack visibility of your IT environment. Depending on its configuration, one syslog-ng server can collect more than half a million log message per second from thousands of log sources.
Duration: 02:35

Learn how DT Asia found security and partnership with One Identity
Watch this short video to hear how DT Asia found unexpected benefits from partnering with One Identity and syslog-ng, including delivering enhanced security solutions to its customers and receiving far-ranging benefits for its own business operations.
Duration: 04:12
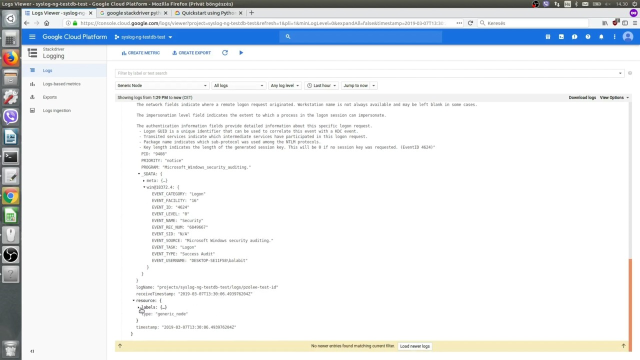
How to efficiently send log data to Google Stackdriver, Part 1
Learn the basics of how to configure syslog-ng Premium Edition to work with Google Stackdriver. This high-level overview uses a simple configuration to show you how to collect and analyze log data, and forward it to Stackdriver. Watch the video now.
Duration: 02:42
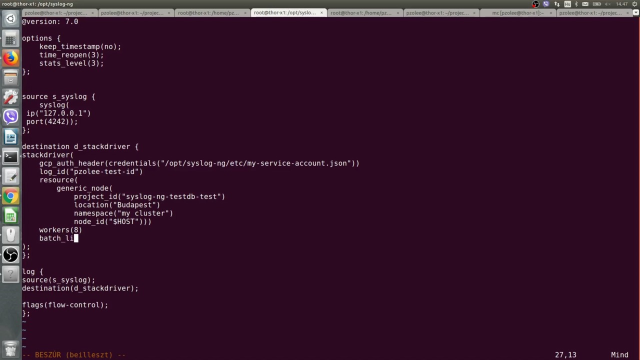
How to efficiently send log data to Google Stackdriver, Part 2
Learn more about using syslog-ng Premium Edition to efficiently feed your log data to Google Stackdriver. This video adds a little complexity to the configuration to highlight more of syslog-ng’s log management capabilities. Watch the video now.
Duration: 02:25

