The syslog-ng Store Box (SSB) appliance is built upon syslog-ng Premium Edition (PE). SSB inherits most of syslog-ng PE’s features and makes them available with an easy-to-use graphical user interface. There are multiple ways how users can authenticate when using SSB. Recent versions also introduced federated single sign-on (SSO) via OpenID Connect (OIDC).
The SSB appliance can collect log messages from many different log sources, in many formats. These include UNIX / Linux / Windows system logs, firewall and router logs, various application logs, and now SQL sources as well. SSB can parse, rewrite, filter, and store log messages. In addition to the traditional syslog-ng features, the SSB appliance provides an interface to search log messages, and does complete log life cycle management, including archiving and backup. Finally, it can also forward events to various on-premises and cloud destinations. It allows you to optimize your SIEM installations both for resources and licensing, as you can collect log messages in a single step, store them on SSB, and only forward a reduced subset of logs to various analytics tools.
OIDC SSO
OIDC is a method to implement SSO and is basically an identity layer built on top of the OAuth 2.0 authorization protocol, using a RESTful HTTP API and a JSON data format.
How does it work? When a user opens a web application (in our case: SSB), the browser is redirected to an Identity Provider. The Identity Provider will prompt the user to log in if they aren’t already authenticated. Once the credentials are validated, a token is sent back to the web application. The token is validated by SSB, and the user is granted access.
In case of SSB, the admin user is always authenticated locally. All other users can use SSO. You can use, for example, OneLogin by One Identity as the Identity Provider solution.
Before you begin
Version 6.10 of the SSB appliance was the first one to support federated SSO via OIDC. However, SSB features receive performance and bug fixes, even minor feature enhancements after the original feature releases. Thus, it is recommended to always use the latest feature release. If you do not have SSB yet, download the 30-day free trial at https://www.syslog-ng.com/register/115581/
Configuring and testing SSB
Once you have SSB up and running, adding SSO support is easy. Before doing the actual configuration, you must collect the following key information from your SSO Identity Provider:
-
Provider URL
-
Client ID
-
Client Secret (in case of Basic authentication)
On OneLogin, you can find these pieces of information on a page similar to this:
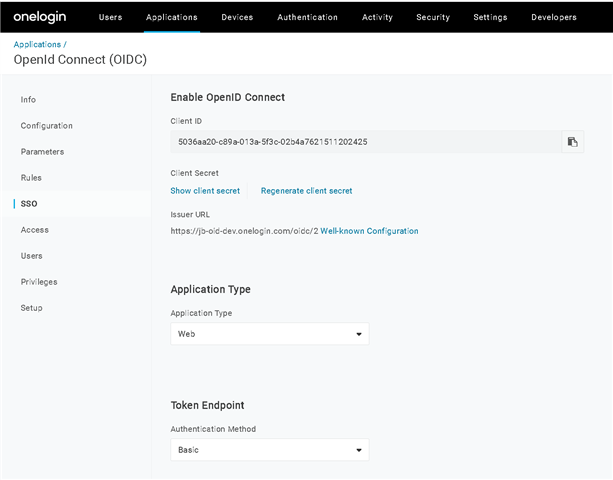
Once you collected these, head over to the SSB configuration interface. In the AAA menu (Authentication, Authorization, and Accounting) click Settings. From the listed authentication methods, choose OpenID Connection. Enter the information you collected previously from your Identity Provider. The SSB configuration then must look similar to this:
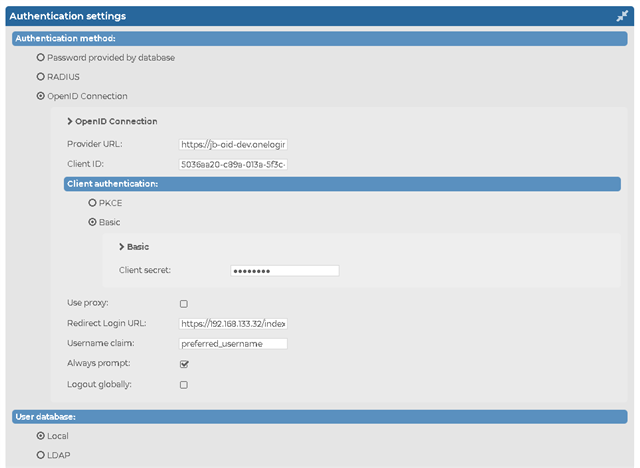
Once you committed your changes, you are ready for testing. Log out or use a different browser and connect to SSB. You should see now an SSO option for login. When you click it, it will take you to your Identity Provider, which will direct you back to SSB after proper authentication.
What is next?
If you want to try SSO support via OIDC in SSB, watch our webcast at https://www.syslog-ng.com/webcast-ondemand/federated-sso-support-with-ssb-via-oidc/ which helps you to set up a test environment and demonstrates SSO with OneLogin in action. It also gives you a good introduction to SSB.


